Resources
The latest insights from the Savvy team & Cybersecurity Space
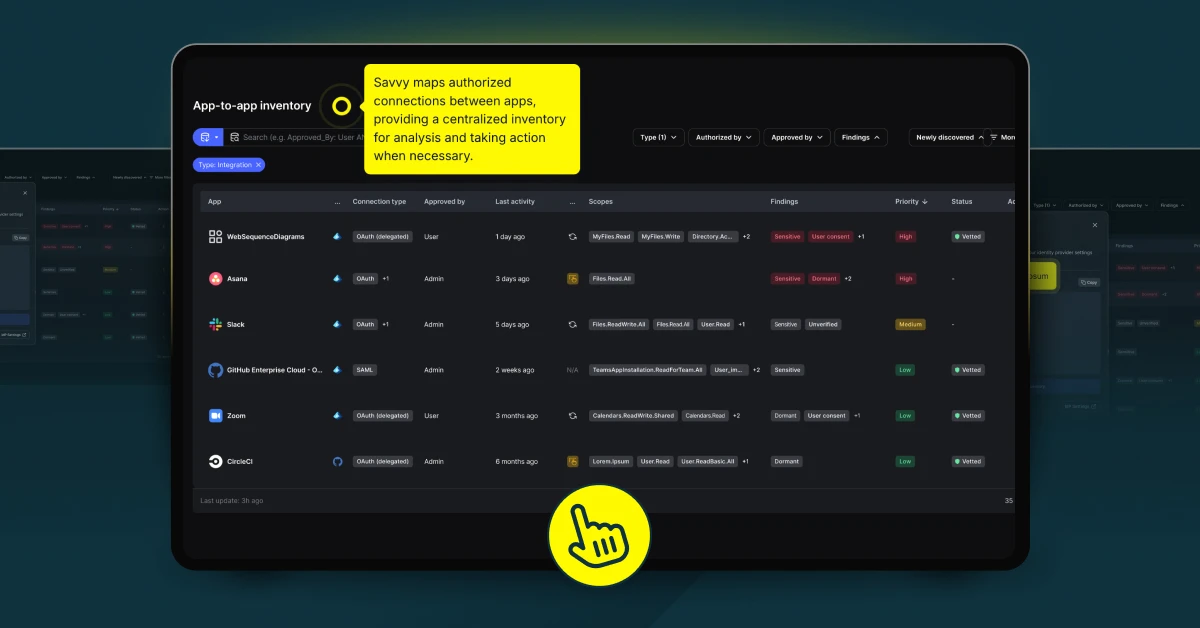
Savvy XGA | Automatic App Onboarding
Identity Governance and Administration solutions were not built for today’s SaaS explosion. API-based connectors cover only a fraction of the apps employees use, slowing projects and leaving gaps attackers exploit. Savvy XGA adds browser-level visibility and seamless integration, extending IGA coverage to hundreds of SaaS and web apps while slashing the manual work typically required […]

Demos
July 11th, 2025
Identity Governance and Administration solutions were not built for today’s SaaS explosion. API-based connectors cover only a fraction of the apps employees use, slowing projects and leaving gaps attackers exploit. Savvy XGA adds browser-level visibility and seamless integration, extending IGA coverage to hundreds of SaaS and web apps while slashing the manual work typically required […]

Blog
June 2nd, 2025
At GCA Technology Services, a top-rated IAM Professional Services provider in North America as recognized by Gartner Peer Insights, we pride ourselves on delivering successful IAM implementations where others fall short. Our deep understanding of the most common pitfalls allows us to proactively address them, ensuring our clients achieve their security and compliance goals. Recognizing […]

Blog
April 21st, 2025
TL;DR: Why Browser-Level Security Should Be Your New Compliance Backbone As SaaS adoption grows and work happens outside traditional perimeters, security and compliance blind spots multiply—especially at the browser layer. Legacy tools miss unmanaged apps, SSO bypass, and incomplete MFA. Browser-level visibility and control fill those gaps. With browser security for SaaS, you can: The […]

Blog
April 8th, 2025
Cyber insurance has shifted from a “nice to have” to a boardroom imperative. As the frequency and severity of cyberattacks continue to rise, organizations across all industries are re-evaluating their risk posture—and insurers are doing the same. What was once a relatively straightforward underwriting process has evolved into a rigorous evaluation of your security program, […]

Blog
April 1st, 2025
An Overlooked Risk in SaaS Security SaaS apps have become the backbone of modern business operations, with enterprises relying on platforms like Microsoft 365, Salesforce, and Zendesk to manage everything from communication to customer support. As organizations adopt more SaaS apps, managing access, security, and compliance across these platforms has become increasingly complex. While IT […]

Blog
March 24th, 2025
Mergers and acquisitions (M&A) are high-stakes business transformations that demand precision, speed, and security. While IT and security leaders are focused on infrastructure and network integration, identity security remains one of the most overlooked aspects of the transition—and that oversight can be costly. The recent Google acquisition of Wiz highlights how major technology deals can […]

Demos
March 18th, 2025
SSO bypass creates dangerous blind spots, allowing users to access critical apps outside your identity provider’s control. With Savvy, you can detect and remediate SSO bypass in real-time, ensuring all identities, logins, and access methods align with your security policies. See how our interactive demo uncovers hidden risks and strengthens your identity-first security strategy.
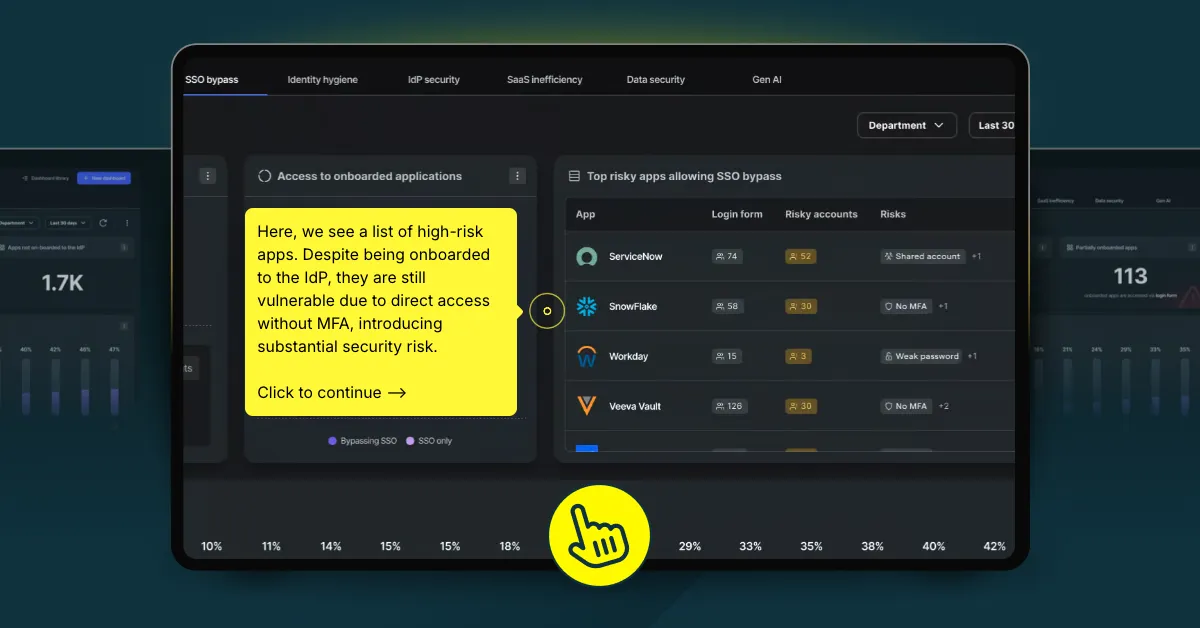
Demos
March 11th, 2025
Discover how Savvy’s uncovers hidden MFA issues and restores control over your most sensitive apps.
