What Is Single Sign-On?
Single sign-on (SSO) is an authentication process designed primarily for user convenience. It allows users to log in once and gain access to multiple applications without needing to re-enter credentials. While this form of centralized authentication does provide some security benefits, such as reducing password fatigue and limiting credential exposure, it is not a standalone security tool. Instead, its main purpose is to enhance usability by streamlining authentication processes across an organization’s digital ecosystem.
How Single Sign On Works
At its core, single sign in relies on an identity provider to verify authentication and grant access to connected applications. Once a user’s credentials are validated, an SSO token is issued, allowing seamless movement between apps without repeated login prompts. The identity provider authenticates the user once, and all subsequent access requests rely on the previously granted authentication session. This reduces login friction and enhances efficiency but does not inherently prevent unauthorized access if other security measures are not in place.
The Benefits of SSO
The benefits of SSO primarily revolve around user experience and administrative efficiency. By reducing the need for multiple passwords, it helps streamline user interactions with applications. It also reduces IT helpdesk costs associated with password resets and improves productivity. However, while SSO centralizes authentication, it does not eliminate the need for other security measures like multifactor authentication and comprehensive access management policies.
How SSO Authentication Works
An SSO system functions by centralizing authentication through an identity provider. When a user logs in, the SSO process generates a secure token that confirms authentication and grants access to authorized applications. This token contains encrypted data that verifies the user’s identity and permissions. However, if the SSO token is compromised, unauthorized users may gain access to all linked applications, highlighting the need for additional layers of security.
SSO Protocols and Standards
Several industry standards support SSO authentication, including:
- SAML (Security Assertion Markup Language): Used for exchanging authentication data between identity providers and service providers. SAML enables single sign-on by providing a secure means of transmitting identity attributes across different platforms.
- OAuth (Open Authorization): Facilitates secure access without sharing credentials. OAuth is commonly used for social login functionalities, allowing users to authenticate via third-party identity providers such as Google or Facebook.
- OpenID Connect: A layer built on OAuth to verify identity using an authentication protocol that is widely adopted in modern web applications.
- Kerberos: A trusted protocol for strong authentication within enterprise networks. Kerberos enhances security by encrypting authentication requests, making it resistant to eavesdropping attacks.
- Lightweight Directory Access Protocol (LDAP): Enables centralized identity management by allowing authentication requests to be processed through a directory service.
Types of SSO Implementations
There are different types of single sign-on tailored to various needs:
- Enterprise SSO: Used within organizations to unify authentication across apps, ensuring seamless access for employees while maintaining high levels of usability.
- Web SSO: Provides seamless login across web-based applications, reducing the need for repeated authentication when accessing multiple online services.
- Federation-based SSO: Links separate systems using federation protocols like SAML and OAuth, allowing authentication across different organizations or cloud environments.
SSO Security Risks
While centralized authentication provides convenience, it introduces significant security risks, making it an incomplete security solution on its own. Some key risks include:
- Compromised SSO Credentials: If an attacker gains access to a user’s account, they can access all linked applications without further authentication barriers.
- False Sense of Security: Not all logins to SaaS applications are routed through centralized authentication tools. Many SaaS providers allow local accounts and consumer logins, which can bypass protections. Preventing these types of unauthorized authentication attempts varies widely depending on how each application is developed and implemented.
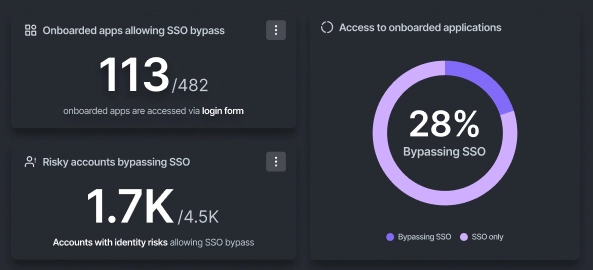
Dashboard visualization illustrating apps where observed SSO Bypass has occurred. - SSO Token Hijacking: If a session token is intercepted, an attacker can reuse it to gain unauthorized access to multiple systems.
- Inconsistent Security Policies: SSO implementation across different applications may vary, leading to gaps in access management and inconsistent enforcement of security policies.
- Reliance on a Single Point of Failure: If the service experiences downtime or is compromised, users may be locked out of all connected applications, causing business disruption.
- Lack of Granular Access Control: SSO simplifies authentication but does not provide fine-tuned access control for different roles and permissions.
To mitigate these risks, organizations should implement additional security measures such as multifactor authentication, session timeouts, monitoring of user behavior, and restrictions on alternative login methods.
How Authentication Tokens Work
SSO authentication relies on authentication tokens to verify user identity. These tokens store identity information and expire after a set duration to prevent unauthorized access. Tokens operate by securely transmitting authentication data between applications and identity providers, ensuring secure communication without exposing passwords. However, token mismanagement can lead to unauthorized access if session expiration policies are not strictly enforced.
Integrating SSO with Access Management
Organizations combine SSO with access management solutions like Active Directory Federation Services (ADFS) to enforce role-based user access policies. This integration allows administrators to define access levels based on job roles, ensuring that only authorized users can reach sensitive systems.
SSO and Password Management
By reducing reliance on multiple passwords, SSO lowers IT support costs and improves user convenience. However, it does not eliminate the need for strong password policies. Users still require a secure set of credentials for centralized login, and weak passwords in an IAM system can still compromise security.
Choosing an SSO Provider
Selecting an SSO provider involves evaluating usability, security, compatibility with existing systems, and compliance with regulatory requirements. Solutions from Microsoft and other vendors integrate well with enterprise infrastructure but must be supplemented with additional security controls.
Top 5 SSO Providers:
- Okta – A leading cloud-based provider with strong integration capabilities and security features.
- Microsoft Entra (Azure AD) – Provides seamless authentication for Microsoft and third-party applications.
- Google Workspace SSO – Ideal for organizations using Google services, offering native integration with Google apps.
- Ping Identity – Enterprise-grade centralized authentication with extensive security options.
- JumpCloud – A robust centralized authentication solution with adaptive authentication and user access management features.
Frequently Asked Questions (FAQs)
1. Is SSO a security tool?
No, SSO is primarily a tool for convenience. While it provides some security benefits, such as reducing password fatigue, it must be supplemented with other security measures like multifactor authentication.
2. Can SSO be bypassed?
Yes, not all logins to SaaS applications are routed through centralized authentication. Some applications allow local or consumer logins, which may bypass SSO protections. The ability to prevent such logins depends on how the application is developed and implemented.
3. What happens if an SSO provider experiences downtime?
If an SSO provider goes down, users may be unable to access connected applications. To mitigate this risk, organizations should have backup authentication methods in place.
4. Does SSO eliminate the need for passwords?
No, SSO reduces the number of passwords a user needs to remember, but it does not eliminate them entirely. Users still need a strong password for their SSO login, and additional security measures should be enforced.
5. How can I improve security when using SSO?
To enhance security, organizations should implement multifactor authentication, monitor user activity, enforce strict session timeouts, and ensure that alternative login methods are restricted where possible.
Conclusion
Implementing SSO simplifies user authentication and enhances convenience. However, it is not a dedicated security tool. Organizations adopting SSO solutions must supplement it with other security measures, such as multi factor authentication, to mitigate potential security risks and ensure comprehensive protection.